Sha Hash Cracking
Fast online lm hash cracking. Engine is back online - cracking 24/7. Insert hashes (16 or 32 chars long) - each in separate line.
SHA256 is a cryptographic hash function, commonly used to verify data integrity, such as its use in digital signatures. Passwords are frequently hashed and saved, without needing to store a password in plaintext. This provides an extra layer of security as a hash is not ‘reversible.’ It’s a one-way function, and each hash is unique (with the exception of collisions, but that’s out-of-scope for this tutorial.)
For this instance, let’s say we’re trying to recover a password (Apples123) that’s been hashed with SHA256 (a5fca64a1ecdce7bbf5cd75d59e302776cfea0c202ed82d6ef42e37ef3d34479).
We want to recover that password because we forgot it. There’s many different types of attacks we can use against a hash, namely dictionary attacks and bruteforce. Let’s say that we have a rough idea of how long the password was, and we know that there are no special characters (!@#$^*). If we wanted to run a plain bruteforce attack, this would take ages. Because of the data that we know, we are able to optimize a much more efficient attack at calculating the original value of the hash. We are able to set a custom character set, and set a specified range of possible lengths of our password.
For the past couple of weeks the latest version of CACHATTO, CACHATTO SecureBrowser for Mac, and CACHATTO SecureBrowser for iOS were released. With these releases, the following contents were added / updated. CACHATTO SecureBrowser for Mac V3.9.0 was released on 4th December 2018. CACHATTO SecureBrowser is an application developed for enterprises, allowing employees to remotely access corporate systems. E-Jan is the developer of CACHATTO, which supports remote connections to its corporate end users' internal file servers via BYOD system through the provisions of high-level security and application support. CACHATTO SecureBrowser is a secure digital workspace application which enables secure onsite and offsite access to business systems on smartphones, tablets, PC and Mac devices. CACHATTO SecureBrowser Provides a secure environment in where corporate resources such as email, calendar, portal sites, file server, cloud-based resources and others could be accessed from within the corporate network or off-site. Cachatto secure browser for mac windows 10.
Using a mask attack (when applicable) can significantly improve your odds at recovering the password. We can reduce the cracking time from thousands of years to a couple hours. Enter Hashcat/OclHashcat (Ocl is the CUDA/OpenCL implementation of hashcat, accelerated by a GPU to utilize it’s parallel processing ability and hundreds-to-thousands of cores.) Hashcat is also able to utilize multi-threading, in addition to certain instruction sets that are advantageous to this type of operation (Intel: AVX/2 and AMD: XOP.)
Let’s start out by grabbing a copy of Hashcat from their website here.
I’ll start out by running a benchmark to get a ballpark idea of how fast we can crack our hashes.
I used the following command (I chose the AVX2 binary because of my i5 processor, and you may use the standard hashcat or the XOP for AMD):
You would think he would want to make up for it. Especially how he mentioned that he felt the last couple shows in Vancouver were sub par. Chad vangaalen blogspot full.
Using the -b option, hashcat will run a benchmark for various hashing algorithms. We’re only interested in SHA256, which comes out to about 24M attempts a second. In the real world, there are many factors that will slow us down, so realistically, we should not expect this speed.
So we have our hash, we have some limited information about our password, and have our tool ready for work. Let’s begin.
Inside the directory you extracted hashcat too, we’ll create a simple plaintext document. I’ll name it hash.txt. I’ll add our hash value calculated earlier to this text file.
The hash of our target password
Okay, we’ve got our target hash saved, let’s get to work. Hashcat can crack dozens of different types of hashes from WPA to NTLM/LM. It can also handle salted hashes, passwords, etc… Again out of scope but relevant to know.
We’ll need to find the option for SHA256.
As you can see, we’ll be using 1400 for plain SHA256. Remember that mask attack I was talking about? That’s attack type ‘3’. We know our password starts with a capital letter, is 9 characters in length, and has 3 numeric characters. In a real world scenario, we might not know any information, but when we do, we can use it to our advantage is massively reduce the time needed to crack the hash. Here’s what our attack will look like:
./hashcat-cliAVX2.bin-m1400-a3--pw-min9--pw-max9hash.txt-ocracked.txt'?u?l?l?l?l?l?d?d?d' |
We ‘-m’ for hash type (1400 = SHA256), ‘-a’ for attack mode (3 = bruteforce/mask), –pw-min and max for our specified length, hash.txt for our hash to be cracked, ‘-o’ will output the hash when cracked to cracked.txt, and finally our mask. ?u is the character set for capital letters, ?l is lowercase letters, and ?d is numbers.
We’ve cut our time down to about three and a half hours to crack our hash. We can optimize our attack even more if you know that specific characters will be in a certain place. Let’s say a password only uses the letters ‘A-F’. We can create a custom character set by using -1 ABCDEF and then using ?1. We can also throw numbers in there too with -1 ABCDEF?d. Do you see what I’m doing here? Let’s say we want to do a second custom character set with lowercase and uppercase letters, we’d do -2 ?u?l and ?2. Since we already used -1, we’ll used -2. Now you can really see the power of this attack.
In order to save a bit of time, I optimized my character set to only use ‘pples’ (I’m cheating, but doing so to demonstrate the power of a mask attack.) The end result will look like this:
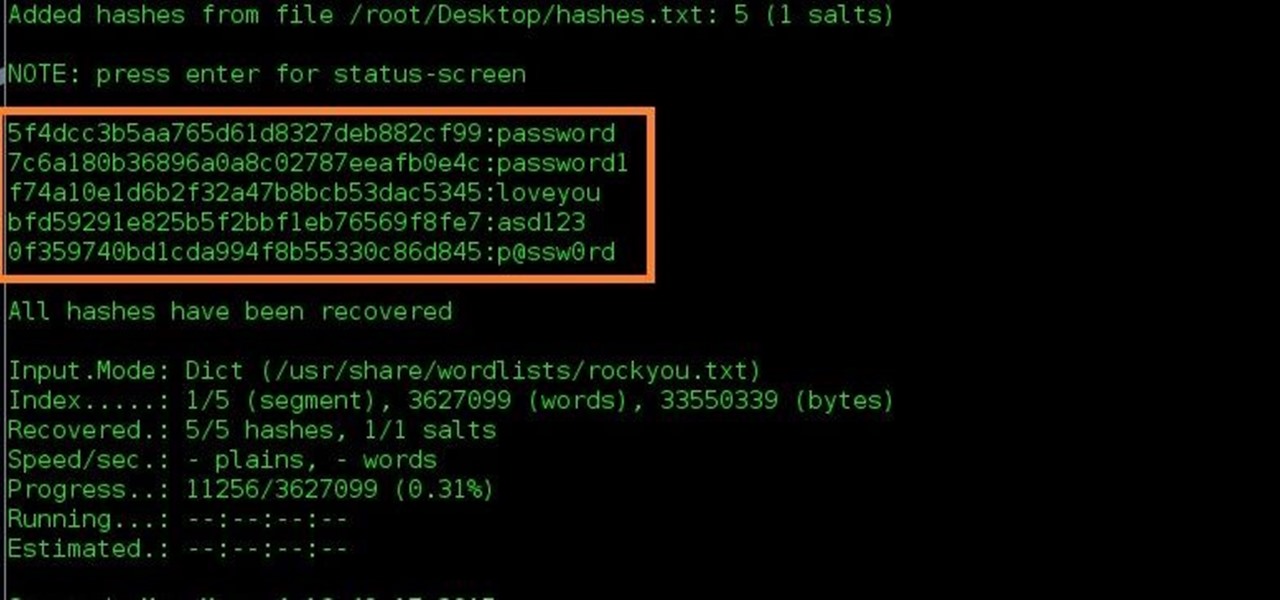
Result of hash cracking
And finally, our cracked hash:
And we’re done! If we were to use a GPU like an AMD7970, we could crack this in mere minutes, as GPU cracking is magnitudes faster.
(This article will be undergoing significant improvements in the next couple of days to organize the information and present it in a better format, along with some better examples and definitions.)
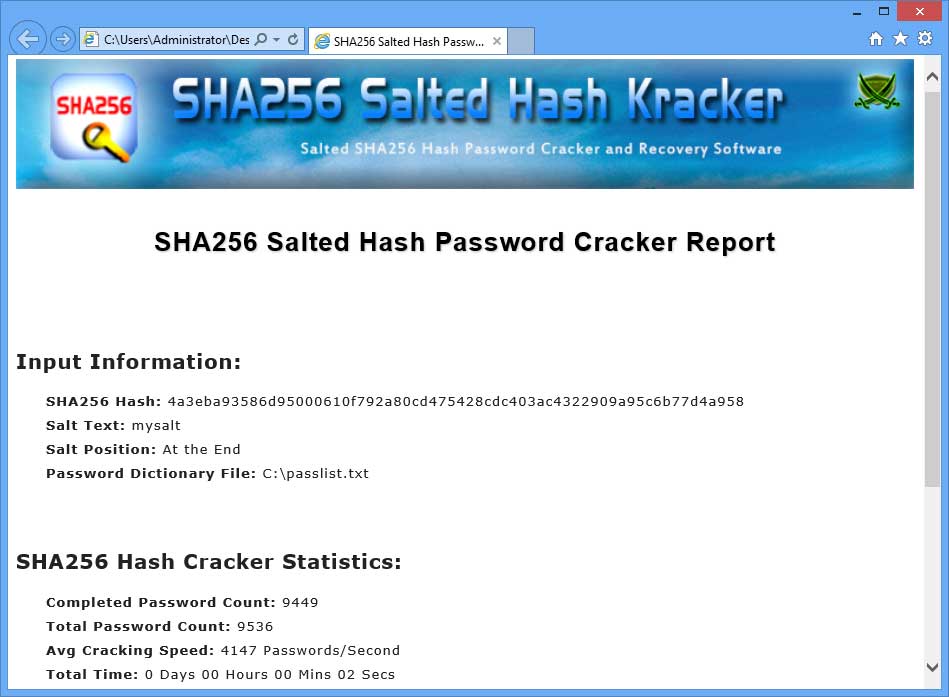
Contents. New v1.6AboutSHA256 Salted Hash Kracker is the free tool to crack and recover your lost password from the salted SHA256 hash.These days most websites and applications use salt based SHA256 hash generation to prevent it from being cracked easily using precomputed hash tables such as. In such cases, 'SHA256 Salted Hash Kracker' will help you to recover your lost password from salted SHA256 hash.It uses dictionary based cracking method which makes the cracking operation simple and easier. By default small dictionary file is included but you can find good collection of password dictionaries (also called wordlist) &Though it supports only Dictinary Crack method, you can easily use tools like, to generate brute-force based or any custom password list file and then use it with 'SHA256 Salted Hash Kracker'.It also allow you to specify the salt position either in the beginning of password sha256(salt+password) or at the end of the password sha256(password+salt).